
Hlcnc-3319 CNC Stone Countertop Sink Hole Router Cutting Polishing Machine - China Stone Polishing Machine and High Precision Polishing Machine
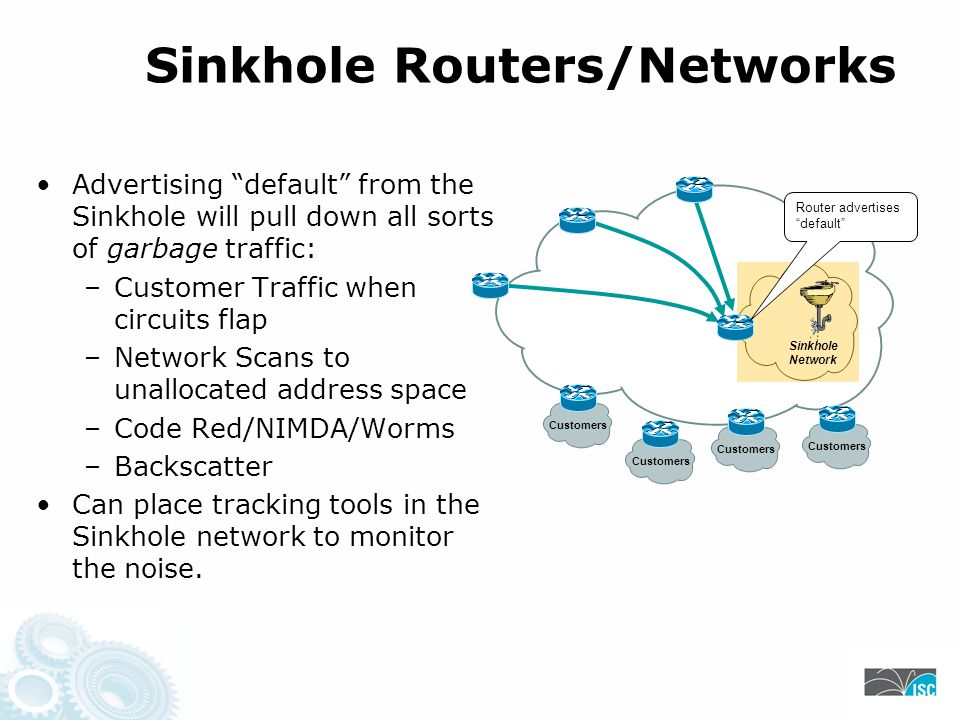
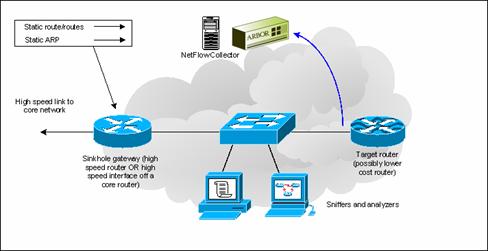
Sink Holes 111. Sink Hole Routers/Networks Sink Holes are a Swiss Army Knife security tool. –BGP speaking Router or Workstation that built to suck in. - ppt download

Cheap Multifunction Marble Granite Countertop Sink Hole Cutting Polishing Machine CNC Router Stone Carving Engraving Machine|Wood Routers| - AliExpress

SoS-RPL: Securing Internet of Things Against Sinkhole Attack Using RPL Protocol-Based Node Rating and Ranking Mechanism | SpringerLink

An IP Traceback Protocol using a Compressed Hash Table, a Sinkhole Router and Data Mining based on Network Forensics against Network Attacks - ScienceDirect
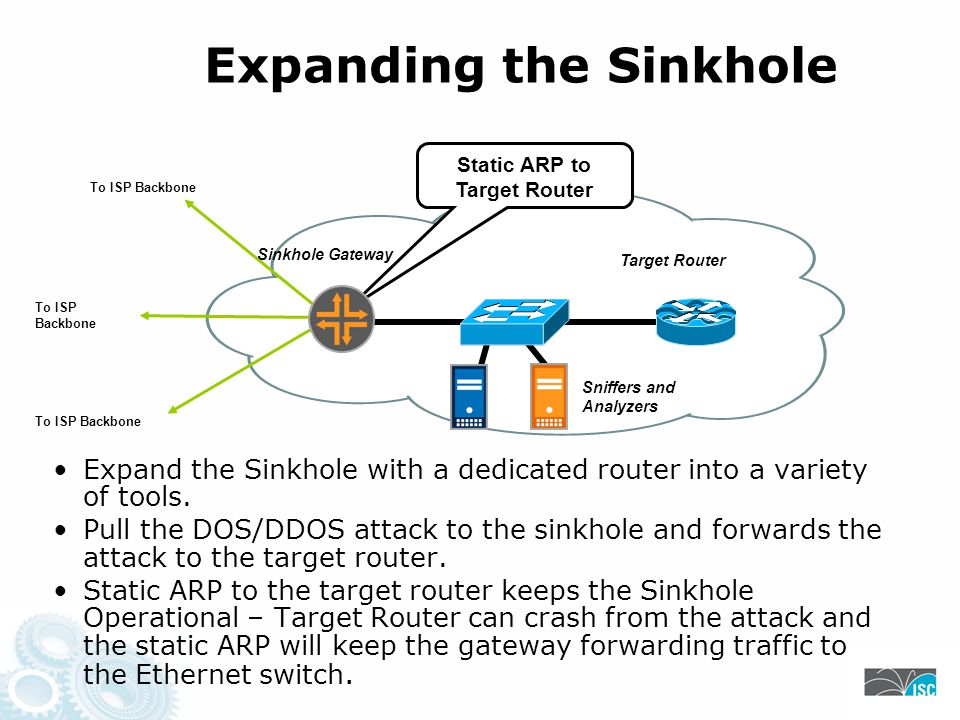
Sink Holes 111. Sink Hole Routers/Networks Sink Holes are a Swiss Army Knife security tool. –BGP speaking Router or Workstation that built to suck in. - ppt download

AN ENHANCED SECURE ROUTING ALGORITHM AGAINST SINKHOLE ATTACK IN WIRELESS SENSOR NETWORKS | Semantic Scholar

Asia Pacific Construction 1 Inch Diamond Finger Milling Bit Full Bullnose Profiler Wheel V25 Router Stone Marble Granite Concrete pad Ceramic Porcelain Edge treartment Sink Hole polishing enlarging: Amazon.com: Tools & Home

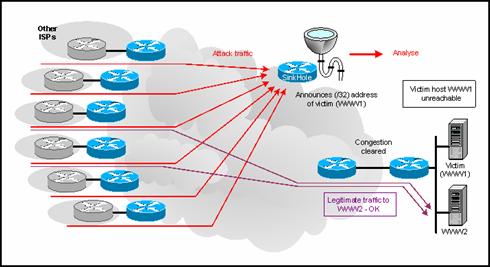



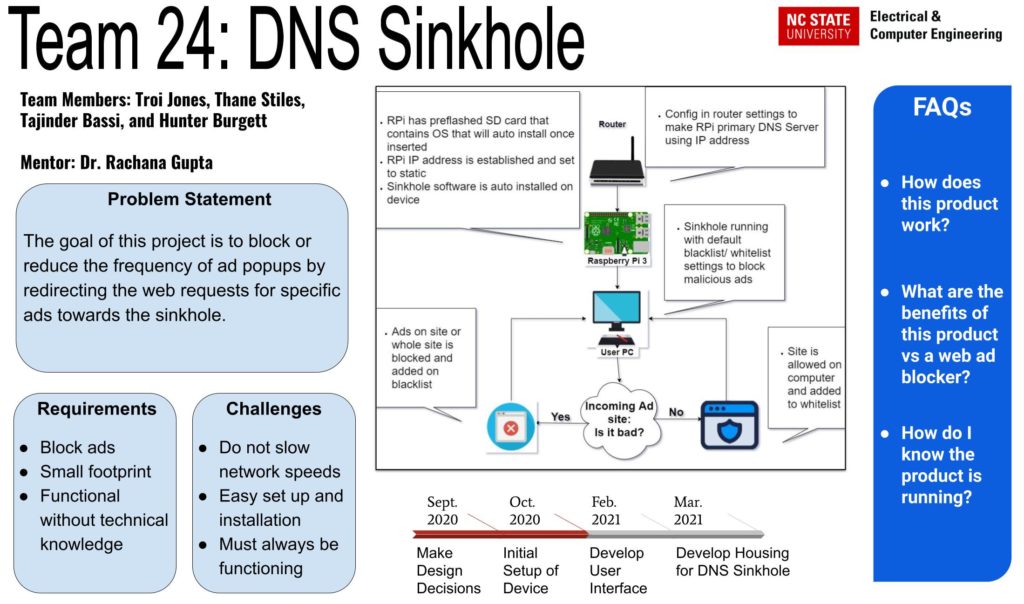





![PDF] Upshot of Sinkhole Attack in DSR Routing Protocol Based MANET | Semantic Scholar PDF] Upshot of Sinkhole Attack in DSR Routing Protocol Based MANET | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/beba485789f622566880e6e244acc195754750d0/3-Figure3-1.png)

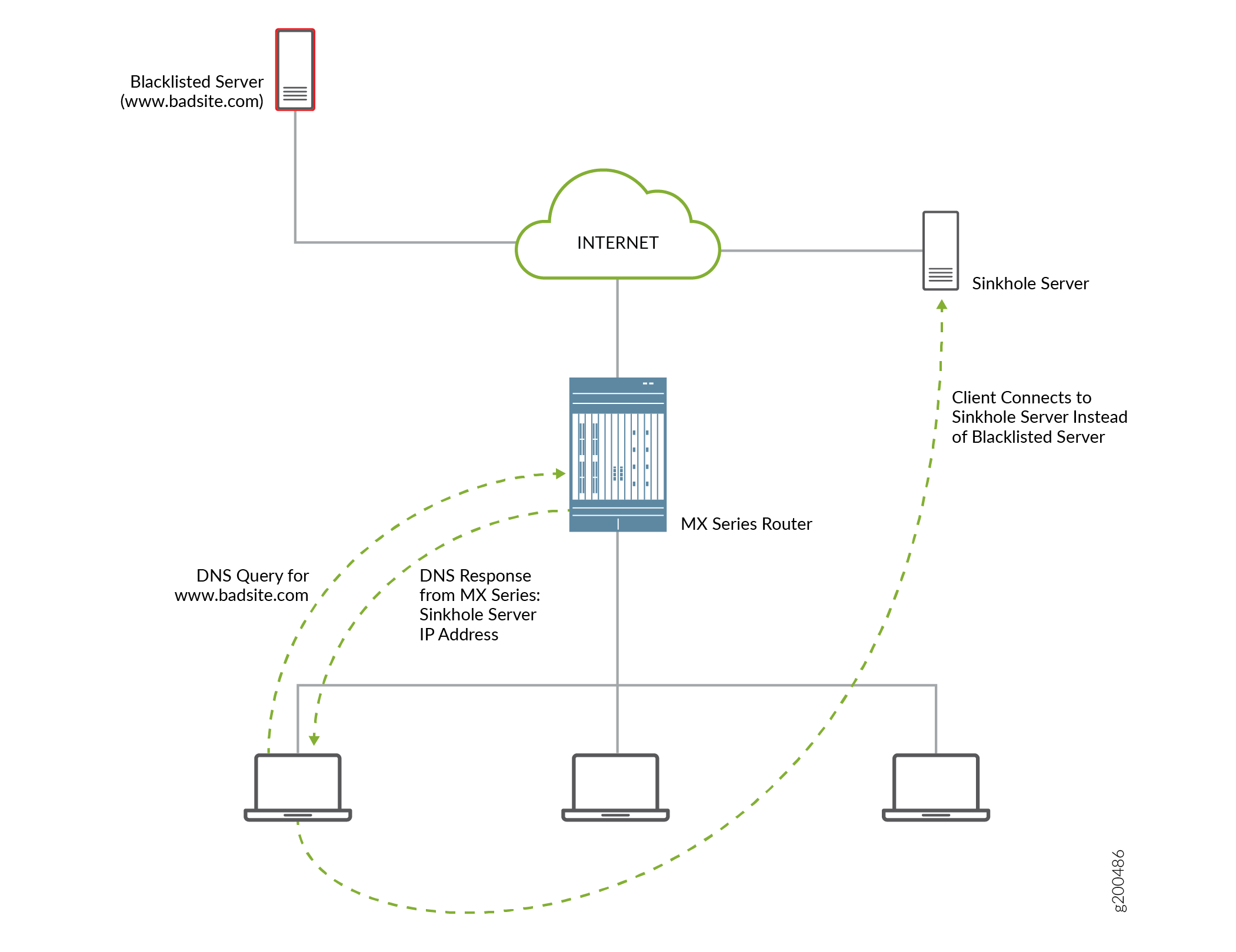
![Understanding DNS sinkholes - A weapon against malware [updated 2021] | Infosec Resources Understanding DNS sinkholes - A weapon against malware [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2020/10/DNS-Sinkhole06262014.gif)